Unix Generate Encryption Key Pair
Posted By admin On 12.12.20GNU gpg is encryption and signing tool.
- Here is a list of best free RSA key generator software for Windows. Using these freeware, you can generate RSA key pair i.e. A pair of public and private keys which are used in encryption and decryption. To create a pair of asymmetric keys, you can specify a key size such as.
- The server uses a separate public and private key to establish this connection. Also, as SSH key pairs are used to authenticate users on a server, each user will have their own public and private keys for this purpose. Generating a SSH key pair. OpenSSH comes with a tool called ssh-keygen to generate key pairs. By default, it uses 2048-bit RSA.
- To create a key pair using a third-party tool. Generate a key pair with a third-party tool of your choice. Save the public key to a local file. For example, /.ssh/my-key-pair.pub (Linux) or C: keys my-key-pair.pub (Windows). The file name extension for this file is not important.
Generating a Secure Shell (SSH) Public/Private Key Pair. Several tools exist to generate SSH public/private key pairs. The following sections show how to generate an SSH key pair on UNIX, UNIX-like and Windows platforms. Generating an SSH Key Pair on. Apr 08, 2005 GNU gpg is encryption and signing tool. Adblock detected 😱 My website is made possible by displaying online advertisements to my visitors. Ads are annoying but they help keep this website running. It is hard to keep the site running and producing new content when so many people block ads. Please consider Continue reading 'Linux create your own GnuPG private and public key'.
The GNU Privacy Guard (GnuPG or GPG) is a free software replacement for the PGP suite of cryptographic software.
GnuPG encrypts messages using asymmetric keypairs individually generated by GnuPG users. The resulting public keys can be exchanged with other users in a variety of ways, such as Internet key servers. They must always be exchanged carefully to prevent identity spoofing by corrupting public key ↔ ‘owner’ identity correspondences. It is also possible to add a cryptographic digital signature to a message, so the message integrity and sender can be verified, if a particular correspondence relied upon has not been corrupted.
How do I create my own GnuPG private and public key
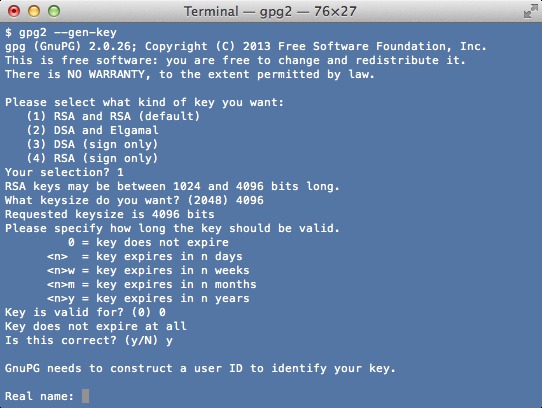
1) Login to your shell account

2) Use gpg command to create the keys$ gpg --gen-key
Output:
3) Now keys generated, you can list your own key using:$ gpg -K
OR$ gpg --list-keys
Output:
Let us try to understand the line pub 1024D/CA7A8402 2007-02-10:
- pub : Public key
- 1024D : The number of bits in the key
- CA7A8402 : The key ID
- 2007-02-10 : The date of key creation
- Vivek Gite : The user real name
- <vivek@nixcraftcorp.com> : The email id
Most important is the key ID i.e. CA7A8402. Make sure you use powerful passphrase to protect keys and not the easy one.
4) To list secret key, type the command:$ gpg --list-secret-keys
Output:
Encryption Key Example
ADVERTISEMENTS
In every SSH/SFTP connection there are four keys (or two key-pairs) involved. This article explains a difference between them and what keys an SFTP client user needs to care about.
The SSH employs a public key cryptography. A public-key cryptography, also known as asymmetric cryptography, is a class of cryptographic algorithms which requires two separate keys, one of which is secret (or private) and one of which is public.1 Together they are known as a key-pair. In SSH, the public key cryptography is used in both directions (client to server and server to client), so two key pairs are used. One key pair is known as a host (server) key, the other as a user (client) key.
A user private key is key that is kept secret by the SSH user on his/her client machine. The user must never reveal the private key to anyone, including the server (server administrator), not to compromise his/her identity.
To protect the private key, it should be generated locally on a user’s machine (e.g. using PuTTYgen) and stored encrypted by a passphrase. The passphrase should be long enough (that’s why it’s called passphrase, not password) to withstand a brute-force attack for a reasonably long time, in case an attacker obtains the private key file.
Different file formats are used to store private keys. WinSCP supports PuTTY format, with .ppk extension.
A user public key is a counterpart to user private key. They are generated at the same time. The user public key can be safely revealed to anyone, without compromising user identity.
To allow authorization of the user on a server, the user public key is registered on the server. In the most widespread SSH server implementation, the OpenSSH, file ~/.ssh/authorized_keys is used for that.
Learn more about public key authentication in general and how to setup authentication with public keys.
Unix Generate Encryption Key Pair Free
Advertisement
A host private key is generated when the SSH server is set up. It is safely stored in a location that should be accessible by a server administrator only. The user connecting to the SSH server does not need to care about host private key in general.
A host public key is a counterpart to host private key. They are generated at the same time. The host public key can be safely revealed to anyone, without compromising host identity.
Unix Generate Encryption Key Pair 1
To allow authorizing the host to the user, the user should be provided with host public key in advance, before connecting. The client application typically prompts the user with host public key on the first connection to allow the user to verify/authorize the key. The host public key is then saved and verified automatically on further connections. The client application warns the user, if the host key changes.
- The text is partially copied from Wikipedia article on Public-key cryptography. The text is licensed under GNU Free Documentation License.Back