Generating A Hash Code From Public And Private Keys
Posted By admin On 12.12.20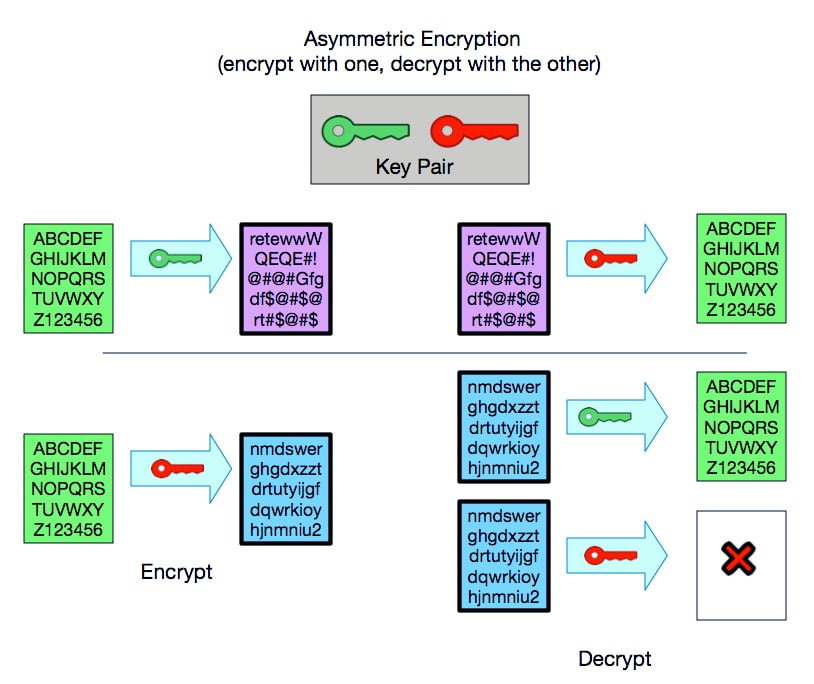
Private Key and public key are a part of encryption that encodes the information. Both keys work in two encryption systems called symmetric and asymmetric. Symmetric encryption (private-key encryption or secret-key encryption) utilize the same key for encryption and decryption. Asymmetric encryption utilizes a pair of keys like public and private key for better security where a message sender encrypts the message with the public key and the receiver decrypts it with his/her private key.

Public and Private key pair helps to encrypt information that ensures data is protected during transmission.
Public/private key pair. Asymmetrical cryptography is a technique that uses pairs of keys: A public key, visible to anyone. A private key, only known to the owner. The private key is essentially a randomly generated number. The public key can be derived from that public key using what’s called Elliptic Curve Cryptography. We can use ECC for encryption, digital signatures, pseudo-random generators and other. Feb 02, 2018 How to generate public and private keys Know something!!! /driver-dr-license-key-generator.html. How to Generate a Private Key from a Bitcoin watch only address. Bitcoin addresses, public key hash, P2PKH transactions.
Generating A Hash Code From Public And Private Keys Work
- RSA (Rivest–Shamir–Adleman) is one of the first public-key cryptosystems and is widely used for secure data transmission. In such a cryptosystem, the encryption key is public and distinct from the decryption key which is kept secret (private). In RSA, this asymmetry is based on the practical difficulty of factoring the product of two large prime numbers, the 'factoring problem'.
- A is created by using a secure hash function to generate a hash value for a message and then encrypting the hash code with a private key. Decryption algorithm. The is.
- Mar 03, 2020 Cloud IoT Core uses public key (or asymmetric) authentication: The device uses a private key to sign a JSON Web Token (JWT). The token is passed to Cloud IoT Core as proof of the device's identity. The service uses the device public key (uploaded before the JWT is sent) to verify the device's identity.
- The general answer is that before the message is signed with Alice's private key, it will be hashed with a hash function of Alice's choice. RSA is not tied to any specific hash function. Alice will include in the header of the message which combination of hash function + signing algorithm she used.
Public Key
Generating A Hash Code From Public And Private Keys For Dummies
Public key uses asymmetric algorithms that convert messages into an unreadable format. A person who has a public key can encrypt the message intended for a specific receiver. The receiver with the private key can only decode the message, which is encrypted by the public key. The key is available via the public accessible directory.
Private Key
The private key is a secret key that is used to decrypt the message and the party knows it that exchange message. In the traditional method, a secret key is shared within communicators to enable encryption and decryption the message, but if the key is lost, the system becomes void. To avoid this weakness, PKI (public key infrastructure) came into force where a public key is used along with the private key. PKI enables internet users to exchange information in a secure way with the use of a public and private key.
Key Size and Algorithms
Generating A Hash Code From Public And Private Keys 2017
There are RSA, DSA, ECC (Elliptic Curve Cryptography) algorithms that are used to create a public and private key in public key cryptography (Asymmetric encryption). Due to security reason, the latest CA/Browser forum and IST advises to use 2048-bit RSA key. The key size (bit-length) of a public and private key pair decides how easily the key can be exploited with a brute force attack. The more computing power increases, it requires more strong keys to secure transmitting data.